Hi,
Today, we will discuss a topic that worries many entrepreneurs: Email Spoofing.
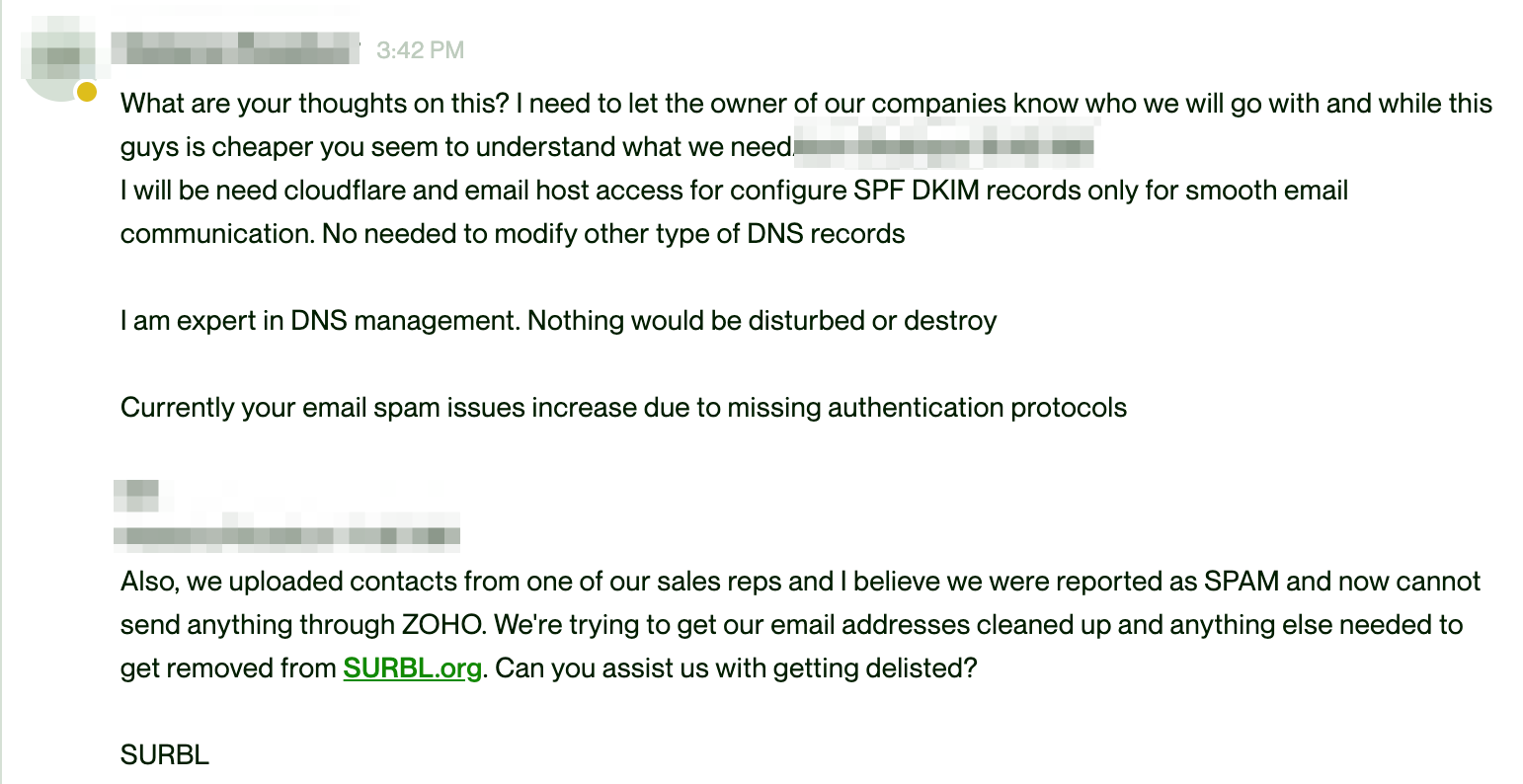
Recently, a client contacted me in a panic. He had discovered messages being sent in his name, even though he hadn’t sent them. A scary situation, right?
You’ve probably heard of Email Spoofing and may have even read a few articles about how to “stop” it from happening. But here’s the truth that few people talk about: you can’t stop Email Spoofing attempts.
Shocking, right? But don’t worry, there is a solution.
The real secret isn’t about stopping the attempts, but making them ineffective.
How do we do that?
- By implementing strong email authentication: Settings like SPF, DKIM, and DMARC are crucial. They allow recipient servers to know exactly what to do when they receive suspicious messages.
- By working together with email service providers: it’s essential to contact the providers involved to implement diligence measures with their users, preventing their infrastructure from being used in spoofing attacks.
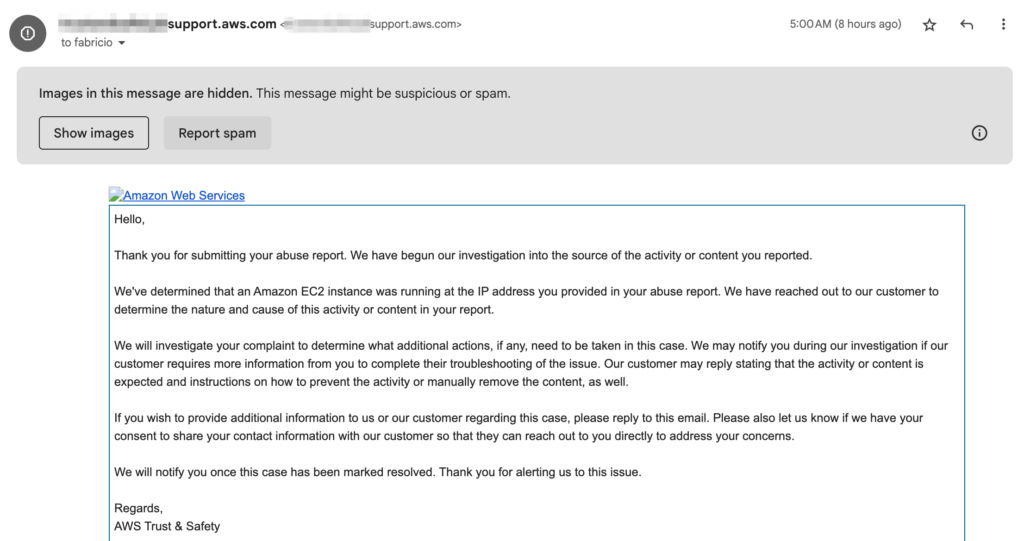
Regarding the case I mentioned, we contacted AWS, and they quickly got back to us, confirming that an EC2 instance was involved in the email flow. This shows how collaboration between companies and providers can be powerful in the fight against Email Spoofing.
Implementing these strategies not only protects your business with external contacts but also prevents spoofing attempts within your own team.
If you’re worried about your company’s email security and want to implement a robust authentication solution, I have a recommendation for you.
Meet Mailguardian360, an Email Infrastructure Authentication and Security solution. With it, I configure and manage your SPF, DKIM, and DMARC policies, making your domain practically invulnerable to spoofing attacks.
Contact me to learn more about Mailguardian360 and how it can protect your business.
Remember: email security isn’t about stopping attempts, it’s about making them useless. And with the right tools, that’s totally possible.
Cheers,
Fabrício
PS1: By the way, there’s something interesting about the image in the AWS email: at the end of August, Google implemented a change in the identification of “tracking pixels,” commonly used to detect when an email message is opened.
When Gmail identifies a potential cold email, it displays a warning that the content is suspicious or spam.
Even though Gmail is focused on protecting user privacy and preventing unsolicited email tracking, especially from cold emails, there may be some overreach. In this case, it was a transactional email, a response to a support request I had opened. While I hadn’t asked to receive a message from the sender’s address, and although it seemed unfamiliar, it was obviously a highly desired message. 🙂
PS2: Photo by Borja Verbena on Unsplash.