Continuing yesterday’s case, where Gmail is blocking the messages from one of my clients, they granted me permission to access their Google Postmaster Tools.
I prepared a report with these points that caught my attention:
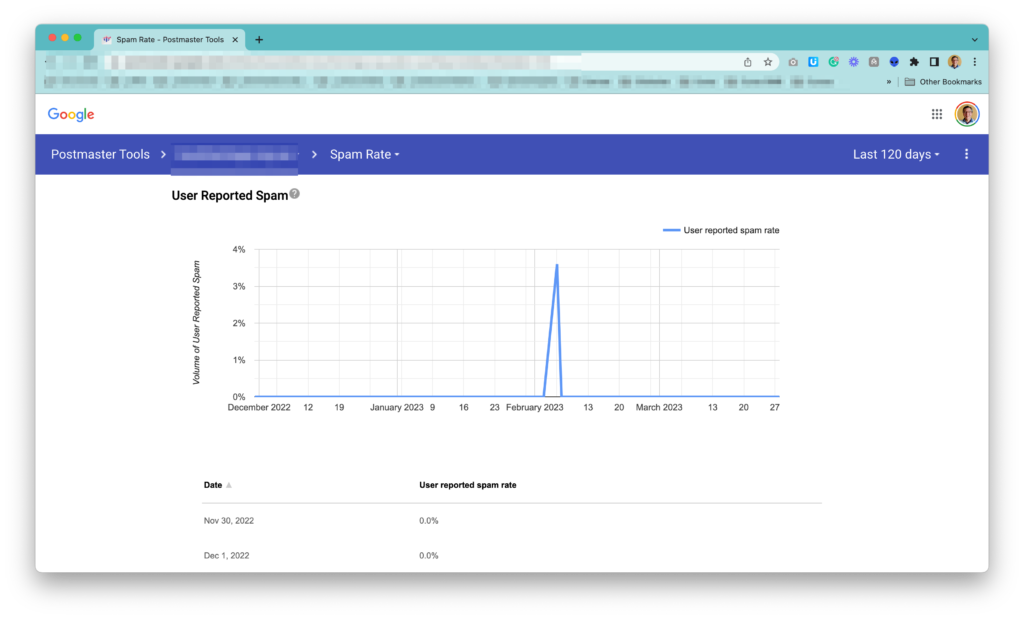
Something unusual happened on Feb 6th: a spike in Spam Complaints from Google’s users. Any clues on what happened on that day?
The DMARC authentication has a lot of failures. Non-authorized people may be using the domain [client’s domain] to send emails. It looks like you have a Barracuda account. Can I access it? I want to look at the logs. Upgrading the policy to “quarantine” (at least) is highly recommended.

A lot of delivery errors to Google’s users happened. As a result, over time, the domain reputation decreased to Medium, and now almost 100% of messages to Google’s users aren’t delivered.
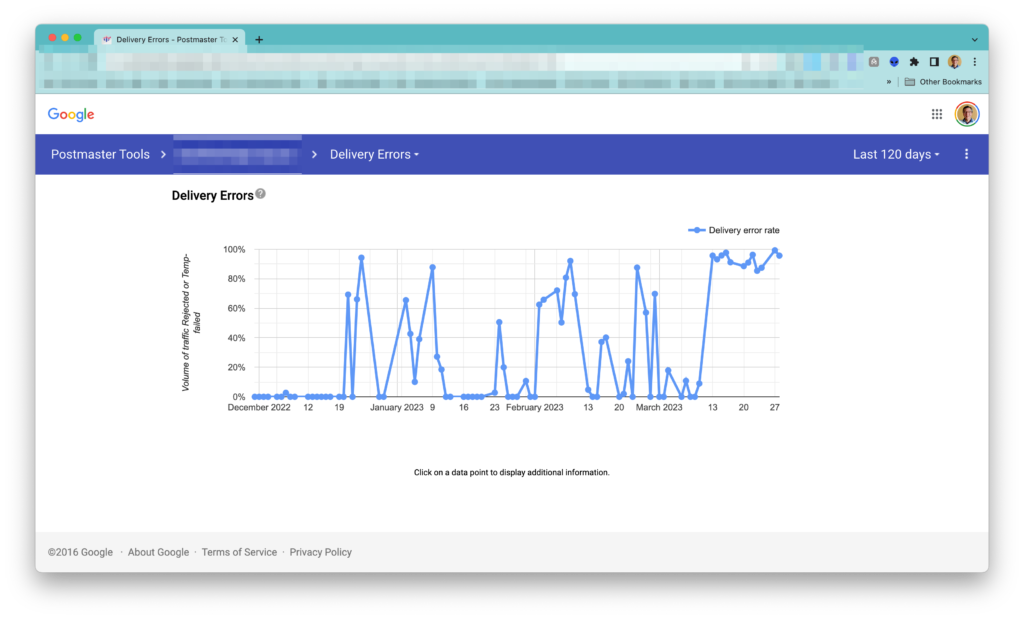
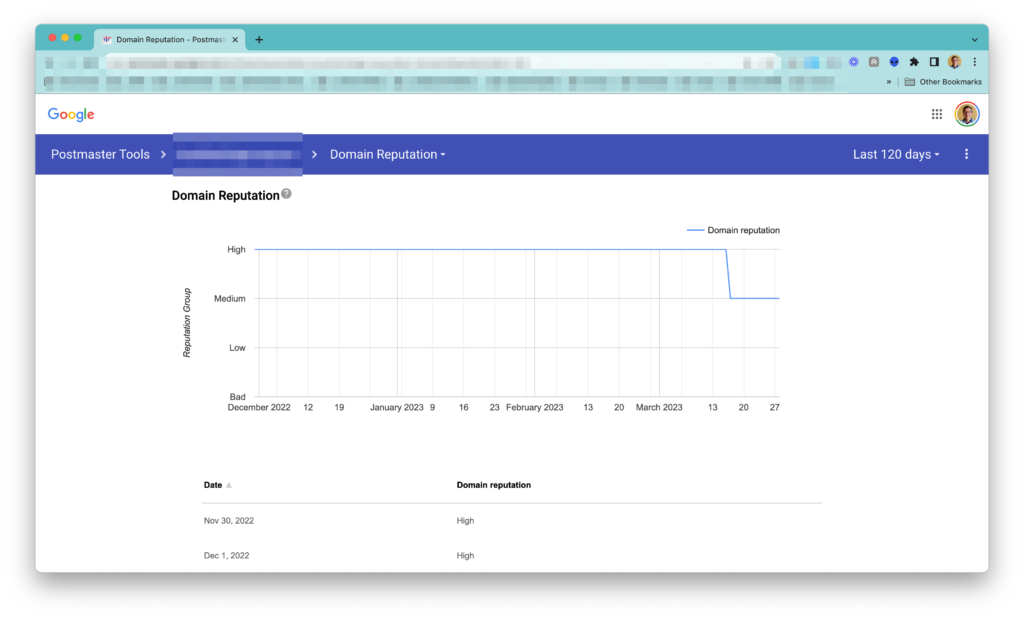
Action items:
- Immediately stop sending to Google’s users; otherwise, the domain reputation will decrease even more.
- Elevate the policy of the DMARC authentication to “quarantine.”
- Investigate the DMARC records. I can perform it if you grant me access.
- Contact Microsoft’s support about the (presumable shared IP) associated with the sender domain. Explain the situation, send them the image below, and tell them the IP reputation had issues recently:

Then, the client forwarded my report to their IT service provider, and these were their responses, along with my comments:
1) [IT service provider] I don’t know if this is going to make a difference, google is blocking [domain] with the rules they have in place, I can’t see how not sending to google is going to change this specific rule, it’s not a reputation block, rather a specific rule block.
[My response] I maintain my recommendation. It’s not about the blocking rule but about the domain reputation. If you keep sending the messages to Google’s users, it will only worsen things.
2) [IT Service Provider] This is easy to do, but I strongly recommend not doing it. This will cause a load of other unexpected email delivery problems. We have tried it before on our own domain and had to move back to logging. Not long ago I asked a number of other IT business owners about this and not one of them had any clients using quarantine or block. The quarantine, block or log is the policy that we set if a spam filter includes a DMARC lookup (not all do) this instructs the receiving filter what to do if the SPF or DKIM records are not correct. It doesn’t just get ignored and blocked anyway, as that would defeat the whole purpose of it. But as there are so many different email filters in use who all work differently this may be part of the problem why DMARC does not work as well as it should.
[My response] I also would maintain my recommendation, assuming there is some monitoring of the received logs. It’s precisely what Microsoft recommends in this article.
If there’s no one monitoring the logs, it’s better not to implement it 🙂
3) [IT Service Provider] DMARC is just a DNS record, it is publicly available, I have added Valimail logging to the DMARC record as it better that the barracuda logs, as you don’t have a paid account with them. DMARC logs are not easy to understand though, and always report DMARC failures for every domain, which I don’t believe are spoofed emails, because the logs are created from responses from a multitude of different filters it just does not work that well, hence the problems that happen when policy is changed to quarantine. It would be great it this worked properly as we would change policy for all of our clients.
[My response] When I said I could investigate, I presumed that some tool was processing the logs and generating a dashboard for analysis. That’s how we do it, and I’m unaware of anyone who does it manually. Due to my poor English, his understanding might have been incorrect. But yes, I want to analyze the dashboard of already processed logs. Do we have it?
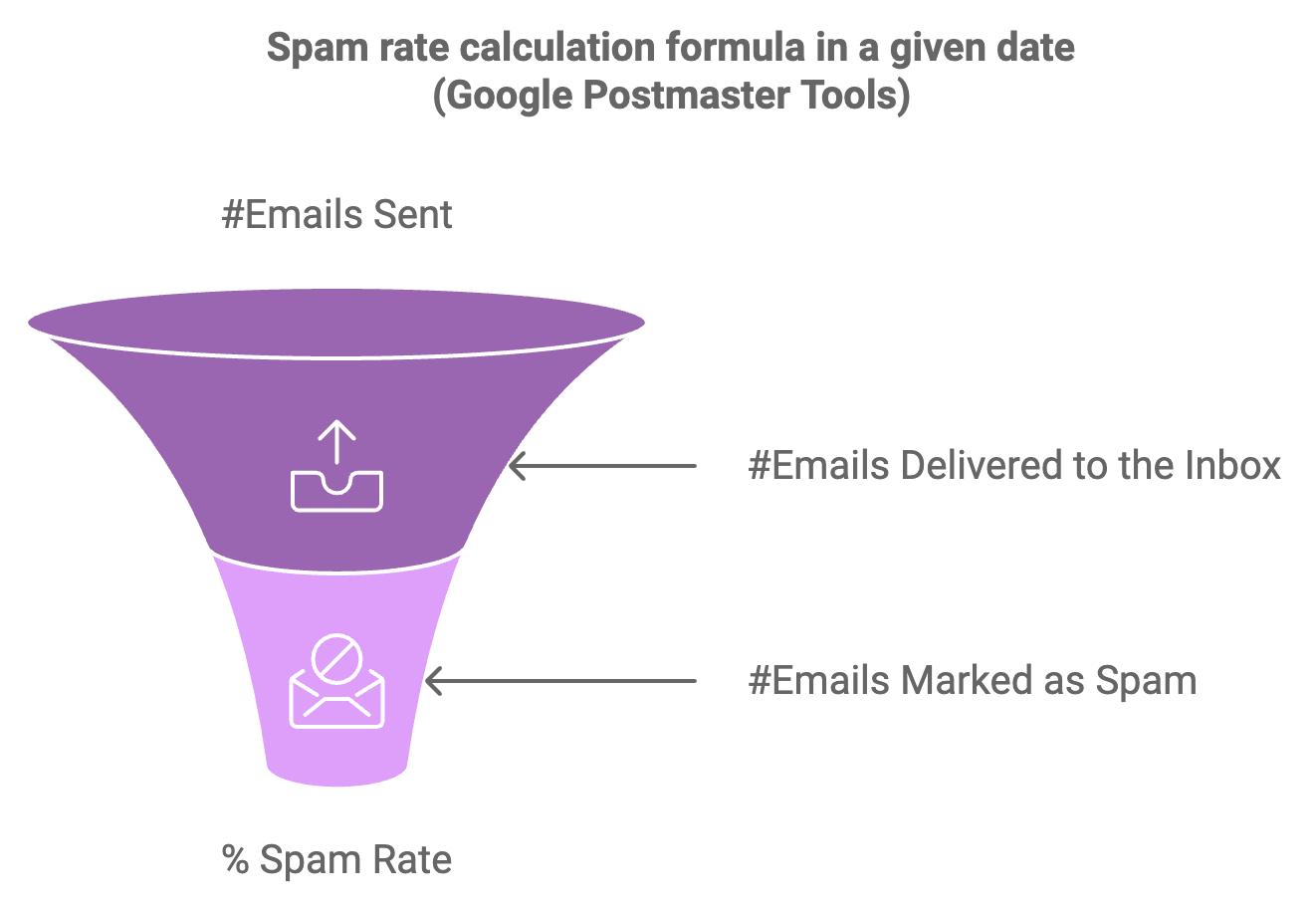
This text worries me: “always report DMARC failures for every domain.” Yes, this happens, but the expected result is that the vast majority should be successful, with a few failures (like the image below). In our case, the scenario is reversed. This is what needs to be investigated. This is DMARC’s value.

One alternative is to direct the logs to a platform I manage, and then I can analyze them directly. This can be done without interrupting the flow of the current tool. We only need to edit a DNS record.
4) [IT Service Provider] Microsoft use hundreds of IPs addresses across multiple gateways when sending from Office 365 to spread the load, it’s constantly a different address. If Microsoft’s IPs had reputation issues, 90% of Australia would be having email delivery problems. We know the issue is with the [client’s domain] and nothing to do with IP addresses. This has been proved, by using an external gateway and that the [client’s domain] can send to google.
[My response] Yes, he’s right. It’s just a “desirable” item, not worth creating friction over.
Finally, I suggested these takeaways:
Item 1) stop sending to Google’s users.
Item 3) edit the DNS record (keeping the current “none” policy) so I can monitor the logs for one week.
I look forward to the next steps in this case 🙂

Comment