Today I bring a case that unfortunately happens quite often: email spoofing. (For example, this is an email that a client I work with received in March 2022.)
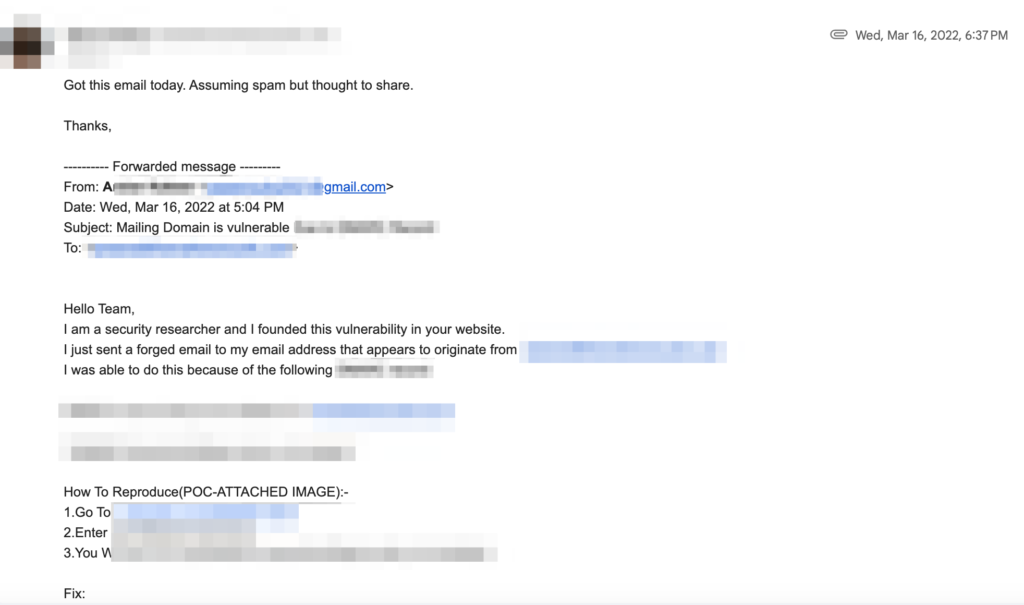
During our discovery meeting, the client told me he was a victim of an email spoofing extortion.
Email spoofing is not something you can stop. However, you can (and should) prevent yourself from being harmed by this malicious practice.
Although email spoofing is a prevalent, persistent threat, there are several ways to protect yourself or your organization from it.
Source: What is Email Spoofing? by Fortinet
An interesting fact: this client has the following email sending infrastructure configuration:
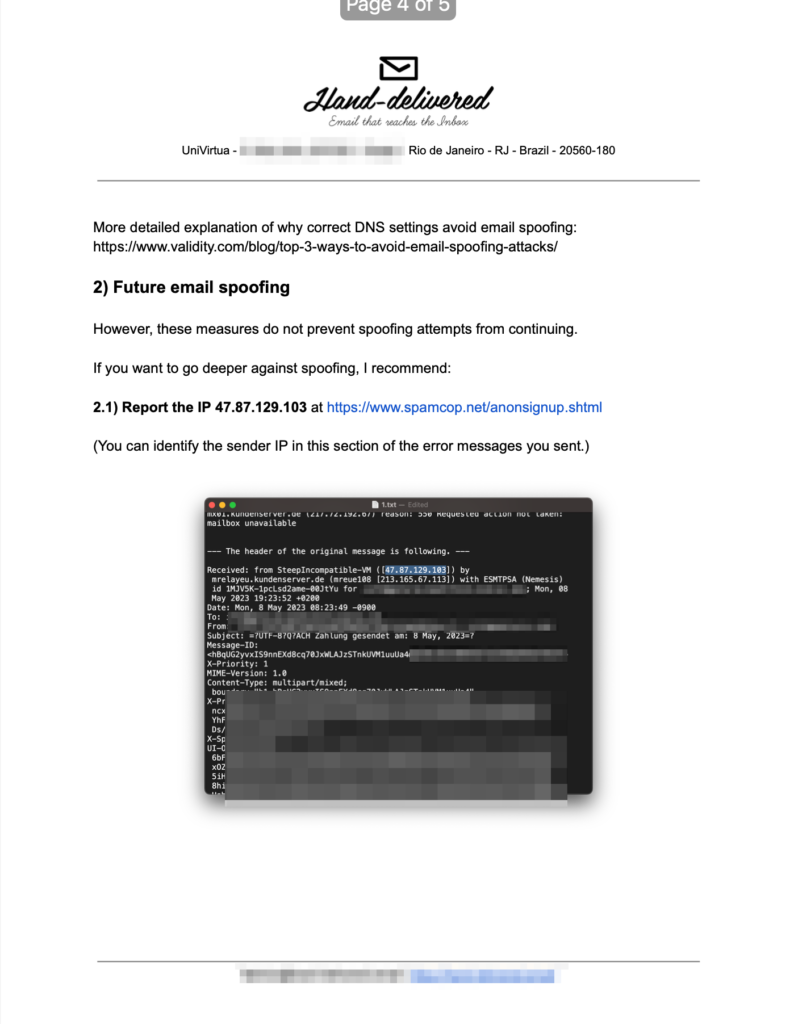
I just want to give you a brief background as well as to what is happening. The email address the spammer is using is _____@_____.com. This email address is created on Ionos servers but it’s not a proper mailbox. Incoming emails are simply forwarded to my gmail account. When I come to send out emails (outgoing emails) from that email address I send them through an email service called SendGrid i.e. my gmail account sends stuff through SendGrid. Hence, when I come to send you the 66 emails you requested (using my gmail), they will be coming from the SendGrid server under the alias _____@_____.com. However, I’m sure the spammer is not sending his emails through SendGrid.
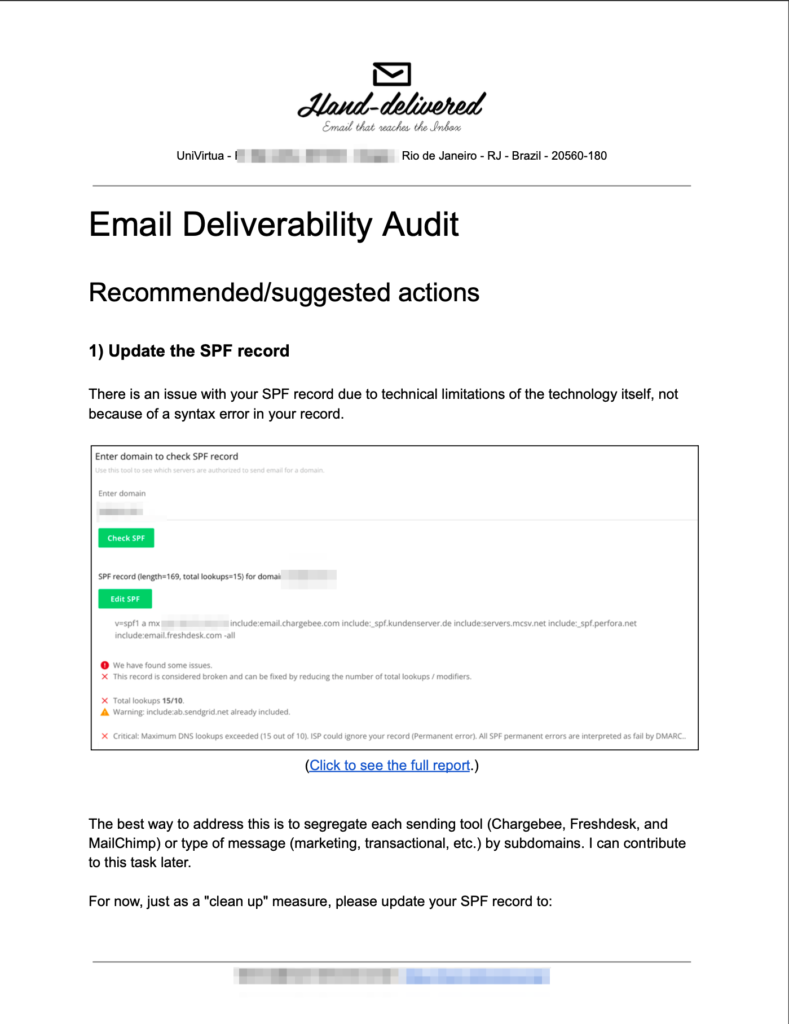
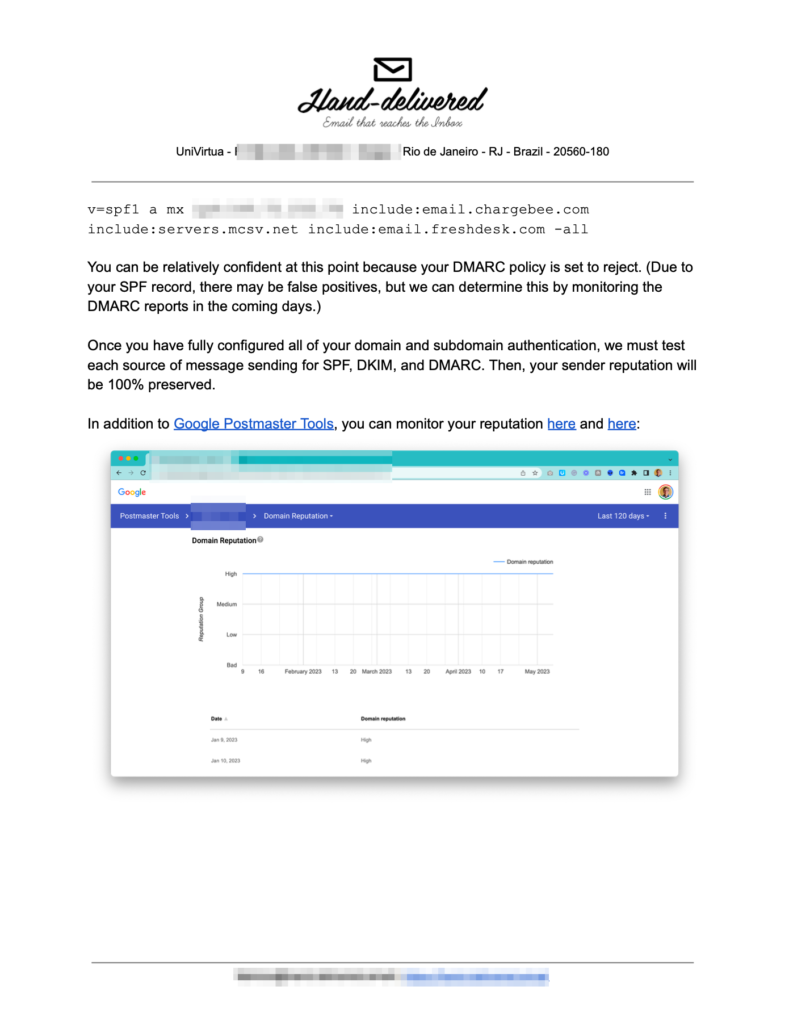
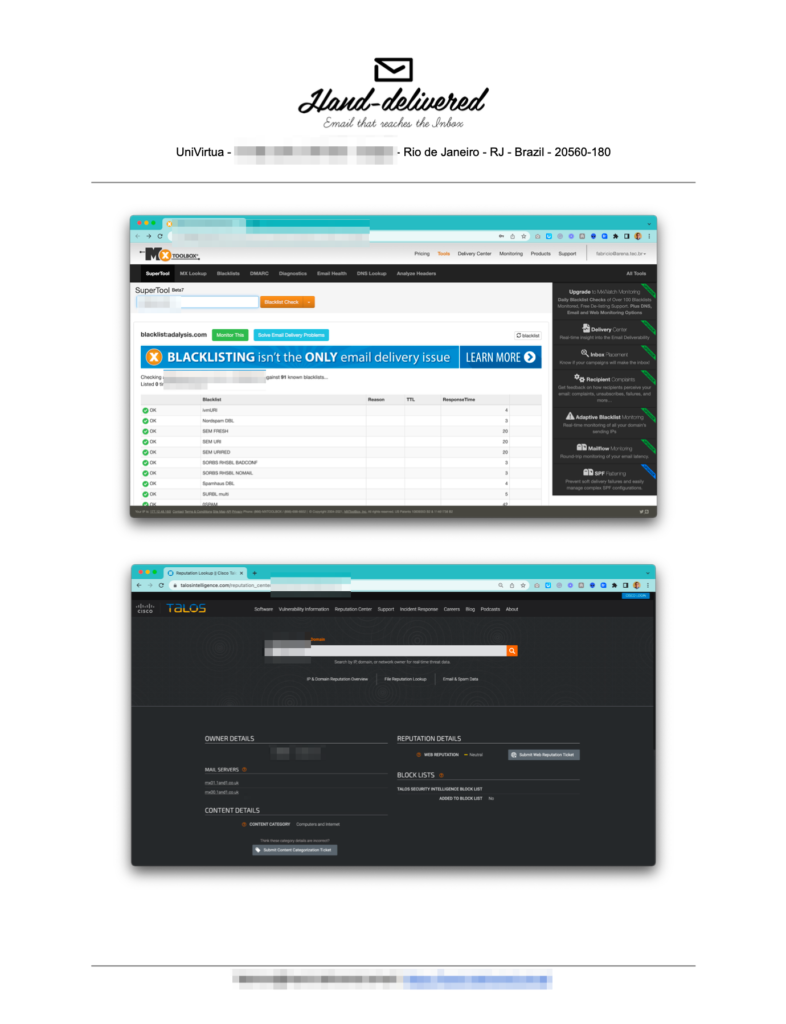
We performed an initial email deliverability audit covering:
- Check the domain reputation in Google Postmaster Tools.
- Collect and process DMARC authentication reports using the GlockApps tool to identify the sources of fraudulent messages.
- Verify SPF and DMARC records.
This initial audit produced the following report:
After receiving the report, the client had a few more questions.
Here’s our dialogue:
The spam emails started again 😞 Any idea how that is possible? I changed the SPF record so was hoping it will stop. But I guess this type of spoofing is always possible. As long as it doesn’t affect our reputation, we don’t care.
[Me] “Exactly 😞 But the most important is that your reputation is preserved.
Important: Maybe I wasn’t emphatic enough, but even with the proposed update, your SPF record still has problems (due to technical limitations, not configuration errors.) To resolve this definitively, it’s necessary to restructure your email architecture and use subdomains.”
I read the article you sent. I thought the new shorter SPF record I used fixes the issue of “too many DNS lookups”. Are you saying our SPF record is still long?
Sorry, yes I used the SPF tool mentioned in the article and see that our SPF record is still too long. I guess we will have to shorten it by doing what you suggested about subdomains. Let’s talk today about this. Thanks
We had a call and clarified his questions and concerns.
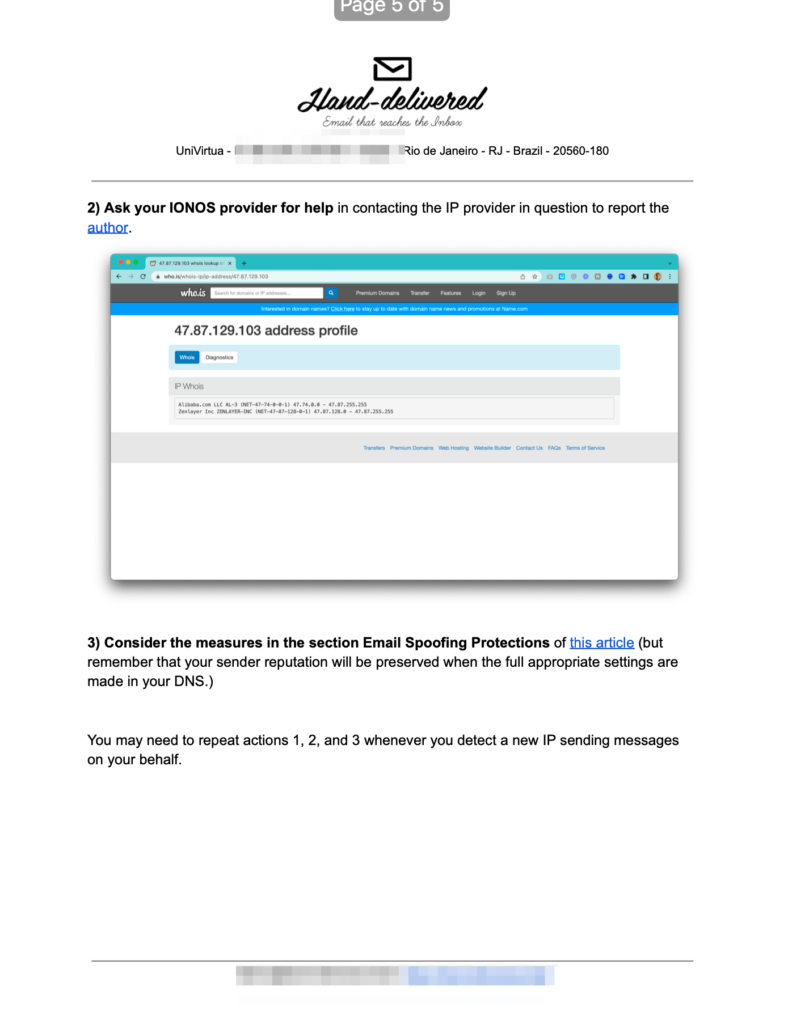
Later, he had more questions.
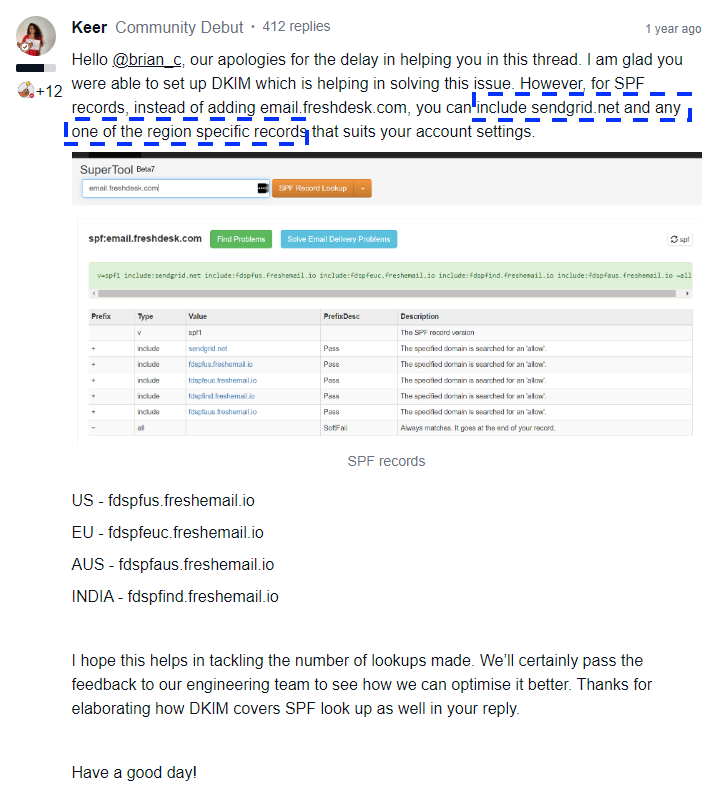
I came across this in freshdesk. IS DKIM an alternative to SPF?
I also found this which suggests the dkim alone is enough.
I also came across this discussion where a lot of freshdesk customers are complaining about this issue. If DKIM can be used instead of SPF this will be the perfect solution for us. Please let me know.
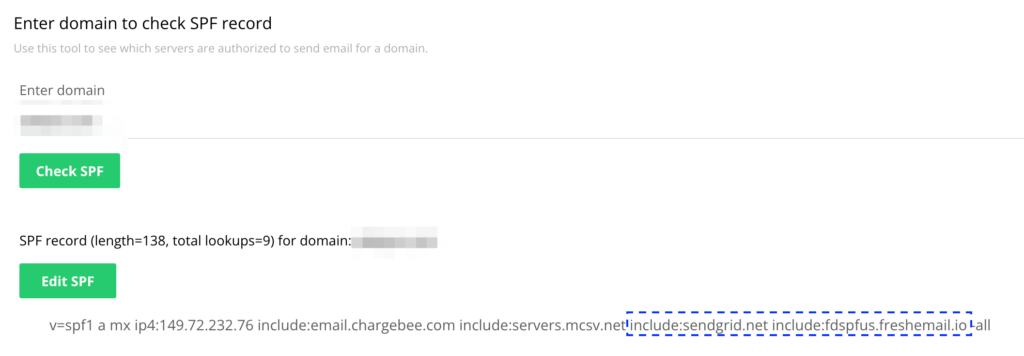
I realized I already have the freshdesk DKIM configured in my DNS. I have 4 CNAME records that point to freshmail. According to the documentation, this means I don’t need an SPF record anymore for freshdesk. Hence, I think I can change teh SPF record from:
v=spf1 a mx ip4:149.72.232.76 include:email.chargebee.com include:servers.mcsv.net include:email.freshdesk.com -all
to
v=spf1 a mx ip4:149.72.232.76 include:email.chargebee.com include:servers.mcsv.net -all
Please advise if this makes sense and can work?
I explained to him: “It can work, but not 100% guaranteed. DKIM and SPF are complementary. There are situations when one will work and the other will not. Overview of email authentication.
I also sent him this reference:
SPF and DKIM address two integral, but discrete, issues central to email security. SPF helps confirm whether an email purporting to come from your company was in fact sent from one of your established IP addresses, and DKIM confirms that the email hasn’t been faked or altered on its way to its intended recipient. So the truth is they are more like frenemies than enemies!
Source: DKIM vs. SPF Email Standards: Do I Need Them Both?
Then, he replied:
Ok if we need both of them, what about the other solution recommended in the post I showed you? See attached. According to this, I can replace the
include:email.freshdesk.com
with
fdspfus.freshemail.ioand it should work. Agree?
My reply: “lmc
Yes, it should work!
v=spf1 a mx ip4:149.72.232.76 include:email.chargebee.com include:servers.mcsv.net include:sendgrid.net include:fdspfus.freshemail.io -all”
He asked a few more questions:
Do I need to include sendgrid again? I thought the IP address is that of sendgrid anyway.
Sendgrid is not just mentioned in the ip4:149.72.232.76, but it’s also looked up as part of chargebee. So my question is why do we need to have “include:sendgrid.net”? Would it not be enough to have only this:
v=spf1 a mx ip4:149.72.232.76 include:email.chargebee.com include:servers.mcsv.net include:fdspfus.freshemail.io -all
My reply: “sendgrid.net is necessary.
If you rely on chargebee.com configuration to include sendgrid.net, it may be removed some day (on changebee side, without you ever noticing) and you will break Freshdesk configuration.”
Today, I sent him the latest update:
“Hello _____,
I hope you are doing well! How are the spoofing messages? They have stopped, haven’t they?
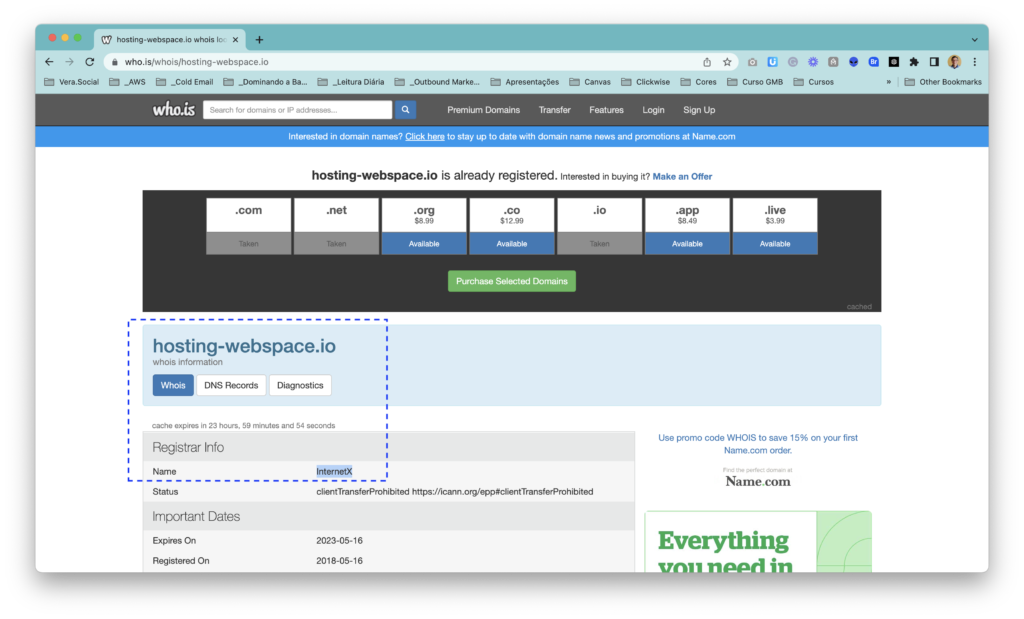
As agreed, I’m attaching the monitoring report received containing yesterday’s data. There is one suspicious server: internetx.com
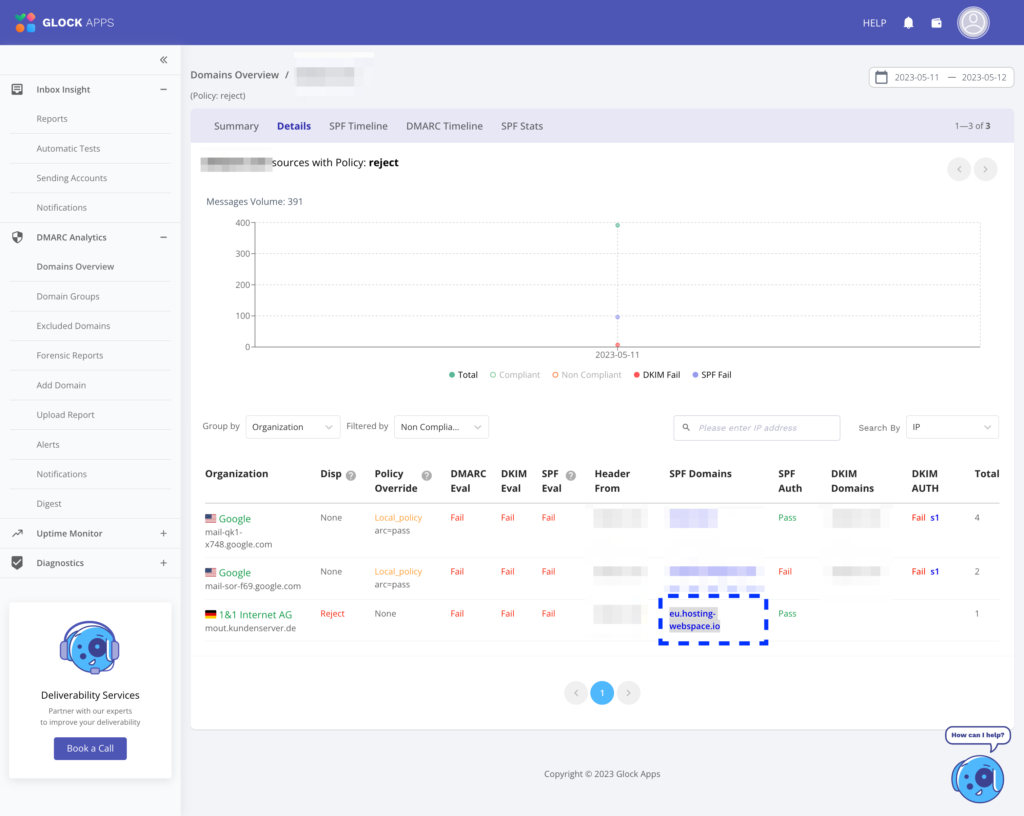
For now, you do not need to take any action. I suggest we continue monitoring. I will review it again on Monday, as we can receive reports with a delay of up to 2 days.
If you see those emails again, please let me know. Remember that your reputation is secure, so there’s no need to feel threatened in any way (the best course of action is to ignore any suspicious contacts and forward the messages to me for analysis.)
Thank you very much,
Fabrício
Then, he wrote me:
The spoofing emails stopped.
What does it mean to see that InternetX thing in our report? Does it mean someone from that host is pretending to be us? I’m not sure what you mean by this being suspicious.
My reply: “It can be someone using that host pretending to be you. Or, it can be that one of your recipients using that host has an automatic forward to another of their email account. That’s why there is no need to take action now.”
(To be continued)
If you have questions regarding email marketing deliverability & strategy, leave your comment below and I will reply.


Comment